Critical levels of detections in the wild
FortiGuard Labs observed a critical level of attack attempts in the wild targeting a 2-year-old vulnerability found on C-DATA Web Management System. Learn More »
Common Vulnerabilities and Exposures
Background
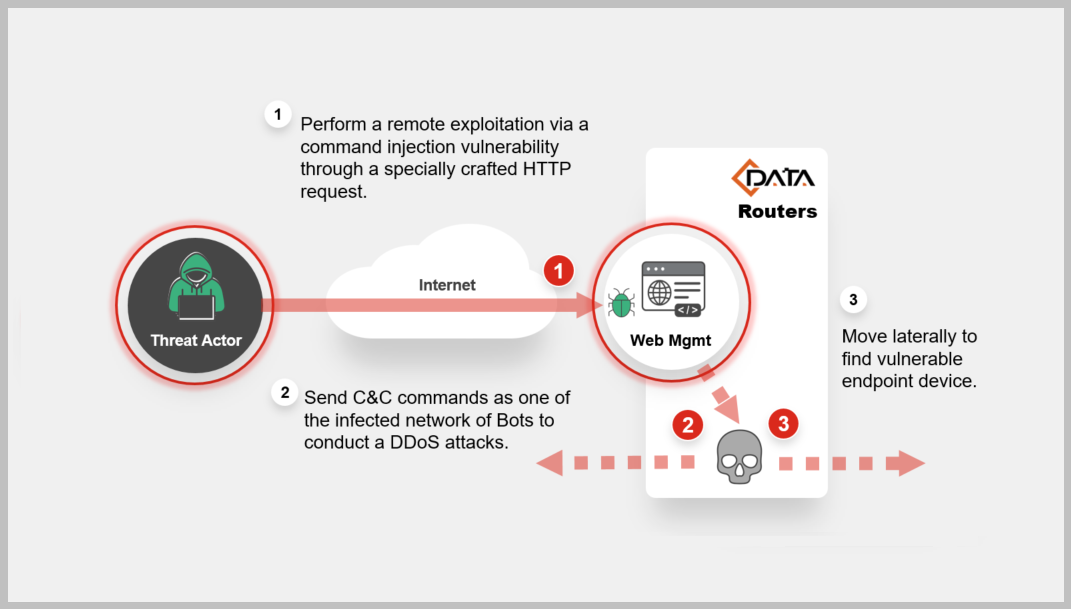
The vulnerability tagged as CVE-2022-4257 allows a remote attacker to execute arbitrary commands on the target system. A remote unauthenticated attacker can send a specially crafted HTTP POST request to the application and execute arbitrary OS commands on the target system. The exploit has been made publicly available; and as of now, we are not aware of any patches available from the vendor.
Latest Development
Recent news and incidents related to cybersecurity threats encompassing various events such as data breaches, cyber-attacks, security incidents, and vulnerabilities discovered.
April 30, 2024: Published the short video.
April 29, 2024: FortiGuard Labs raised the severity from medium to high with the continuous exploitation attempts reaching to almost 50,000 unique IPS devices.
April 25, 2024: FortiGuard Labs observed and blocked attack attempts on 40,000+ unique IPS devices in the week of the release of this outbreak. The majority of the blocked attacks are from IPS devices located in Japan, the United States and Australia.
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
-
AV
-
AV (Pre-filter)
-
IPS
-
Outbreak Detection
-
Threat Hunting
-
Playbook
-
Assisted Response Services
-
Automated Response
-
NOC/SOC Training
-
End-User Training
-
Attack Surface Hardening
-
Business Reputation
Threat Intelligence
Information gathered from analyzing ongoing cybersecurity events including threat actors, their tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), malware and related vulnerabilities.
Loading ...
References
Sources of information in support and relation to this Outbreak and vendor.