The average Hackaday reader hardly needs to be reminded of the incredible potential of the modern microcontroller. While the Arduino was certainly transformative when it hit the scene, those early 8-bit MCUs were nothing compared to what’s on the market now. Multiple cores with clock speeds measured in the hundreds of megahertz, several MB of flash storage, and of course integrated WiFi capability mean today’s chips are much closer to being fully-fledged computers than their predecessors.
It’s not hard to see the impact this has had on the electronics hobby. In the early 2000s, getting your hardware project connected to the Internet was a major accomplishment that probably involved bringing some hacked home router along for the ride. But today, most would consider something like an Internet-connected remote environmental monitor to be a good starter project. Just plug in a couple I2C sensors, write a few lines of Python, and you’ve got live data pouring into a web interface that you can view on your mobile device — all for just a few bucks worth of hardware.
But just because we’re keenly aware of the benefits and capabilities of microcontrollers like the ESP32 or the Pi Pico, doesn’t mean they’ve made the same impact in other tech circles. In his talk Wireless Hacking on a $5 Budget, Alex Lynd goes over some examples of how he’s personally put these devices to work as part of his information security (infosec) research.
When Less is More
Like so many before him, Alex started his journey with Linux on the Raspberry Pi. It was, at least in the days before the chip shortage, a cheap and easy way to start exploring the intersection of hardware and software. But once they got too rare and expensive for a young hacker to experiment with, he started looking for alternatives.
This lead him to the work of security researchers such as Spacehuhn, who had used the ESP8266 to perform various attacks and techniques (such as WiFi deauthentication) which could previously only be done on a computer. While a Linux box filled with all the latest offensive and defensive security tools would of course always have its place, Alex immediately saw the appeal in developing these sort of single-purpose infosec gadgets.

The most obvious one, naturally, is cost. Most modern microcontrollers are so cheap that they’re essentially disposable — something that can be a huge benefit while performing reconnaissance or other penetration testing tasks. If you don’t have to go and retrieve your deployed gear, that’s one less chance to get caught. In a similar vein, the fact that a microcontroller is so much smaller than even a Raspberry Pi makes it easier to hide.
On the subject of covert operations, Alex also points out the potential to commandeer an existing IoT device that may very well already have your favorite chip onboard. We’ve seen plenty of smart light bulbs that used some member of the ESP family internally, and hackers have demonstrated how easily they can be reprogrammed. Crafting a custom firmware for one of these devices that maintains its original functionality while adding in some malicious functions is certainly within the realm of possibility.
Hidden or otherwise, Alex also believes MCUs can be easier to configure and deploy in the wild. If you’re just looking to perform a single task, such as logging all of the devices going into or out of a particular building, you don’t need to configure and run a whole operating system. Without the added complexity of that OS, your deployment can be faster and potentially more reliable. It can also be easier and faster to replicate. Whether your goal is to share your work with others, or simply spin up multiple instances of your own personal tool, it doesn’t get much easier than flashing a firmware file to a fresh MCU.
Targeted Applications
Alex quickly move from the theoretical to the practical, showing off a number of devices he’s built and operated over the last several years.
The first was a discreet reconnaissance tool made up of an ESP-01 hidden inside of a USB phone charger. It could detect when particular WiFi devices were present or had joined a particular network, and alert him with email and SMS notifications. In his case, Alex was just keeping tabs on his father’s comings and goings, but it’s not difficult to see how this capability could be put to use during a penetration test.
He then goes on to describe an expedient WiFi capture device made from nothing more than an ESP32, an SD card, and a salvaged lithium ion battery tucked into an inconspicuous enclosure. Alex explains that the more powerful ESP32 has the ability to perform full WiFi packet capture, which is dumped to a Wireshark-compatible file on the SD card. The device, which looked like any other piece of trash laying on the street, was then able to intercept the communications of a nearby wireless security camera.
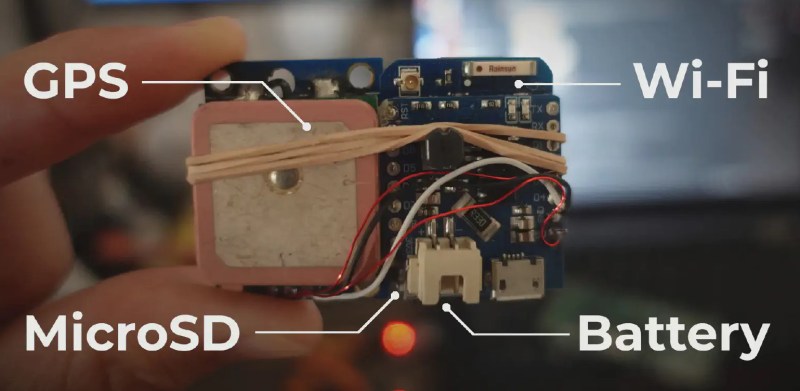
Alex also describes his experiments with a technique known as warshipping, which is when a device is physically shipped to a destination (such as an office building) for the purposes of surveillance or penetration testing. The idea is to send the package to an employee or department that doesn’t exist — you want it to be in the building long enough to capture useful data, but then have it ultimately returned to sender. The catch here is that you need a lightweight device that can run for as long as possible on an internal battery pack. A Raspberry Pi can do it, but in terms of runtime per milliwatt-hour, there’s no beating a modern microcontroller with a properly configured sleep routine.
Going Beyond WiFi
Alex ends the presentation by talking about what’s he has planned for the future. Thus far he’s limited himself largely to WiFi, but he’d really like to start experimenting with other wireless protocols using similar low-cost hardware.
Bluetooth is the next logical step, as several microcontrollers have that built-in. This offers some interesting potential for tracking assets and even individuals, as Bluetooth Low Energy (BLE) has become essentially the defacto communications method for wearable devices. Tracking a target’s phone is one thing, but if you can keep tabs on where their smart watch or earbuds are, you’ll really be able to zero in on their movement.
 Beyond that he’d like to start working with radio modules (or even software defined radio) that will let him tap into the unlicensed frequencies such as 433 MHz, as there’s a whole world of interesting devices out there just waiting to hear the right signal. But Alex is also interested in the potential for using microcontrollers to physically interface with devices, which is where I/O powerhouse platforms like the Pi Pico come into play.
Beyond that he’d like to start working with radio modules (or even software defined radio) that will let him tap into the unlicensed frequencies such as 433 MHz, as there’s a whole world of interesting devices out there just waiting to hear the right signal. But Alex is also interested in the potential for using microcontrollers to physically interface with devices, which is where I/O powerhouse platforms like the Pi Pico come into play.
Ultimately, Alex sees nothing but potential for the use of microcontrollers in information security. Each year they get faster and more capable, while still remaining affordable enough that you can buy a handful just to play around with the various platforms. His high water mark is the Sensor Watch from Joey Castillo: he reasons that if an individual hacker can pack a programmable microcontroller and sensors into such a constrained platform while having the device remain completely inconspicuous externally, imagine what else is possible if you’re willing to really lean into the minimalist approach.















“If you don’t have to go and retrieve your deployed gear, that’s one less chance to get caught.”
If you are leaving your gear in place you will increase the chances your operation will be discovered. While the hardware may only cost $5, the cost of giving your target insights into your TTPs will be heavy.
It might work if you are preserving the devices original function (e.g. an light bulb that looks and works like a light bulb) with the ability to remove your tools from the device at when needed. Although this maybe more effective as a supply chain attack (e.g. all bulbs from a certain country are pre-installed with info-sec tools, etc.).
Interestingly enough if said bulb is WIFI capable and has OTA capability it might be possible to deauthenticate it from current network, connect to your ap, flash malicious firmware and let it run as normal.
Warshipping? Dammit, now I’m going to have to Faraday-cage my company’s mailroom!
I know people like the fat linux on the pi, and all the tools, but really – why would you want a full desktop operating system on your small monitoring device?
RTOS (like on the esp32) is more than enough to get a lot of work done, is easy to write code for and can do things in real time..